Multi-Factor Authentication (KB)
Everything you need to know about multi-factor authentication (MFA): what it is, why it’s important for your security, and how it is used in Texada products.
Quick Reference
- Multi-factor authentication, or MFA, is a security protocol that has gained popularity in recent years due to the fact that it represents a significant increase in security over password-only authentication.
- Multi-factor authentication works by adding a step to the regular login process, requiring users to verify their identity via an external system - for example, entering a one-time login code sent to their email address or mobile device.
- In the coming months, Texada will be implementing email and SMS MFA for its products. As we move closer to implementation, we will provide more information on how to enable and configure MFA for your system.
Introduction
Multi-factor authentication, or MFA, is a security protocol that has gained popularity in recent years as a way to improve security when logging in to websites, apps, and software applications. In the coming months, Texada will be implementing MFA for multiple Texada products, including Web, Mobile, and SRM, to help protect our users’ data and make our software as secure as possible. The following article will tell you everything you need to know about MFA - what it is, how it helps protect you and your data, and what you can expect from this upcoming change to Texada’s software suite.
Why do we need MFA?
Whenever a user accesses a website, app, or software application - such as Texada Web - the system needs some way of verifying that the user is who they claim to be. Historically, this verification has almost always been performed using a password: when the user first creates their account, they establish a secret and hopefully secure password which they can then use to verify their identity when logging into the system again in the future. This is referred to as single-factor authentication, or SFA.
The problem with password-based authentication is that passwords are often not as secure as they need to be to keep users protected from cyber attacks. There are many reasons why this can be the case, including:
- Too-simple passwords: The most secure passwords are long, complex strings of characters with combinations of lowercase and uppercase letters, numbers and symbols. Unfortunately, these are also the hardest kinds of passwords to remember, and many users will opt for simple, easy-to-remember passwords instead. Hackers are aware of the most commonly-used passwords and will almost always try these first when attempting to gain access to someone’s account.
- Password reuse: As users create more and more accounts to access online services, keeping track of all the passwords for these accounts can become daunting. As such, many users will opt to use the same password for multiple accounts to save time and effort. However, this poses a significant security risk, as a hacker who is able to gain access to one account can now easily gain access to additional accounts that use the same password.
- No particular reason: No security system is completely infallible, and hacking techniques are getting more sophisticated every day. From phishing (impersonating a legitimate institution in an attempt to get the user to reveal personal information) to human error (writing a password down on a sticky note or leaving a workstation unattended) to social engineering (using information found on social media to guess the answers to a user’s security questions), there are dozens of techniques hackers can use to penetrate systems and cause damage. While there is no single solution that offers 100% protection from cyber attacks, following security best practices can significantly reduce the risk of experiencing a security breach.
As users move more and more of their personal and professional lives online, it is becoming increasingly important to take every reasonable precaution to keep their data safe and secure. Multi-factor authentication is one such precaution.
What is MFA?
As the name suggests, implementing multi-factor authentication involves adding a secondary authentication factor to the login process. This secondary factor can take a number of forms (see below), but regardless of the type of MFA, the intent is the same: to make it harder for hackers to penetrate the system by requiring something else in addition to a password.
MFA systems typically rely on the involvement of a third party for the additional verification step. For example, SMS MFA involves sending a text message containing a one-use code to the user’s phone. This is a key reason behind MFA’s added security: even if a hacker is able to guess a user’s password, it is highly unlikely they will also have access to the user’s mobile device. As such, MFA is a simple and easy way to significantly increase user security.
How MFA Works
Generally speaking, the login process for systems using MFA is as follows:
- The user enters their username and password on the login page.
- If the username and password are correct, the user is sent a one-time login code via their established MFA method. This code is usually set to expire within a short timeframe, and will be invalidated if another login attempt occurs.
- The user enters their one-time login code on the login page.
- If the one-time code was correct, the user is given access to the system.
Common MFA Methods
Common multi-factor authentication methods include:
- Email MFA: An email containing a one-time login code is sent to the user’s email account.
- SMS MFA: A text message containing a one-time login code is sent to the user’s mobile device.
- Hardware token MFA: The user is given a physical security token - an electronic device similar to a key fob - which generates login codes at regular intervals. Alternatively, the hardware token may plug directly into the user’s device, allowing MFA to happen automatically.
- Software token MFA: The user installs a MFA program on their device which generates login codes as needed. Alternatively, this software may communicate directly with the system to which the user is trying to gain access, allowing MFA to happen automatically.
- Biometric MFA: Instead of using login codes, this method makes use of biometric data - such as fingerprints - to verify the user’s identity.
Texada and MFA
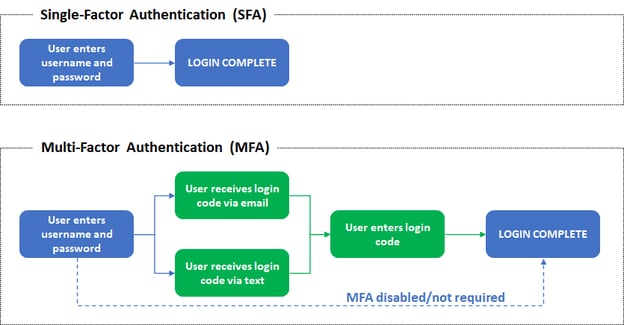
A visual guide comparing the login process for single-factor authentication and multi-factor authentication.
Here are some important details about how Texada is planning to implement MFA:
- Two methods of MFA will be available when logging in to the Texada platform: email MFA and SMS MFA. In order to enable these methods of verification, users will have to provide a valid email address or mobile phone number, respectively.
- Administrators will be able to enable and disable MFA for each user individually.
- The MFA used by Texada software will be adaptive, meaning that MFA will only be required when the system determines that a login attempt is high-risk - for example, when logging in from a new device or when the system has not performed a MFA check in a while.
As Texada moves forward with our MFA implementation, we will provide additional communication on what to expect and how to manage your company’s MFA settings. Stay tuned for more information, and do not hesitate to reach out with any questions.
.png?width=365&height=50&name=Texada%20Logo%20(Black).png)